Cerulean Studios Trillian 3.1 Blank AIM Message DoS
Product:
Trillian Pro and Basic 3.1 Build 121
Released:
02/28/2006
Description:
It is possible to remotely crash Trillian by sending an empty IM with the AOL AIM protocol. This attack is easily repeatable. The attack does not require the Trillian user to accept the message or have the user in their contact list. Trillian will display an incoming message from the attacker, but does not show any text.
The error message upon crash is:
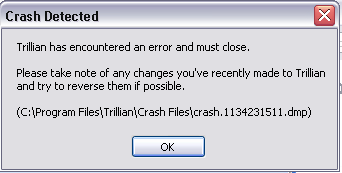
Systems Affected:
Trillian Basic 3.1 Build 121
Trillian Pro 3.1 Build 121
Other Research:
The blank-message attack was tested against several AIM clients without impact:
- Apple iChat (3.1)
- GAIM (1.5.0)
- Adium (0.86)
- AIM Windows (5.9.3861)
- AIM Triton Windows (1.0.2)
Several clients were also tested for blank message problems with the ICQ protocol and had no impact from the attack:
- Trillian (3.1)
- GAIM (1.5.0)
- AIM Windows (5.9.3861)
- AIM Triton Windows (1.0.2)
AOL AIM Mac OSX 4.7 does not crash upon receiving a blank message, however it does trigger the "message received" sound without displaying any new message content. If you actually know anyone using this client and have an active chat with them, you can trigger the sound endlessly and annoy the hell out of them.
Code:
The blankdos perl code allows an attacker to send an empty IM to the victim. It requires the Net::OSCAR module (v1.907).
The username and password to sign onto AIM must be supplied at the start of the script.
The "blankdos" program usage is:
blankdos <Victim>
The script will connect to AIM, and prompt the attacker to press "return" when ready to send the attack. It will then disconnect from AIM.
Fix/Workaround:
Upgrade to version 3.1.0.122 or higher.
Vendor Status:
- Cerulean studios was notified on 02/01/2006.
- Cerulean released 3.1.0.126 of the AOL plugin 02/2?/2006.
- Released on 02/28/2006.
Thanks:
Jericho/attrition.org for being a guinea pig while investigating the Trillian RTF DoS and eventually finding this one, as well as Zel for suffering several unexpected disconnections.
Contacts:
sullo@cirt.net
References:
Updated information can be found on OSVDB.org under the following entry:
| OSVDB-23528 | Cerulean Studios Trillian Blank AIM Message DoS |




